What is Ransomware?

How does a Ransomware work?
Following these steps, you will be able to protect your computer from infections and protect your self, your data, your work and your beloved ones from sad events.
How does a Ransomware work? See the video!
In the following steps you can read advices about what to do to protect your home or office compiters from being encrypted.
How does a computer get infected by Ransomware?
Here are 13 simple answers that will help you keep infections away.
Rule #1: Do you have a Backup?

Not much to say here, this is the most basic rule that you need to follow regardless if there's a chance to be targeted by Ransomware or not. In case you have a recent backup and get attacked by Ransomware, the only thing you have to do is to remove the infection and restore your files from the backup.
Unfortunately, adding a hard drive to your computer and keeping your backups there is not a solid backup plan. The reason is that in case of a Ransomware infection, all local storage means will get targeted and all network devices will get infected too (sometimes even network drives that are not mapped). This means that your local or remote backup storage devices will get encrypted too.
Aurora Ransomware λύση back Up
There are two ways to overcome this: a) Keep your backups to the Cloud, whatever that means (cost, confidentiality issues, slow access) b) Keep your backups to a device that you disconnect after the backup procedure is done.
Rule #2: Do you have a proper antivirus?

Make sure your computer is being protect by a decent antivirus program. We suggest using antivirus, anti-ransomware and anti-exploit software that can analyze your computers behavior and protect you if something starts to behave erratically, even if the infection is from a new strain (zero day tolerance).
Rule #3: Do you update your operating system?

Rule #4: Do you keep your installed software up-to-date?
Rule #5: Are your SPAM filters active?
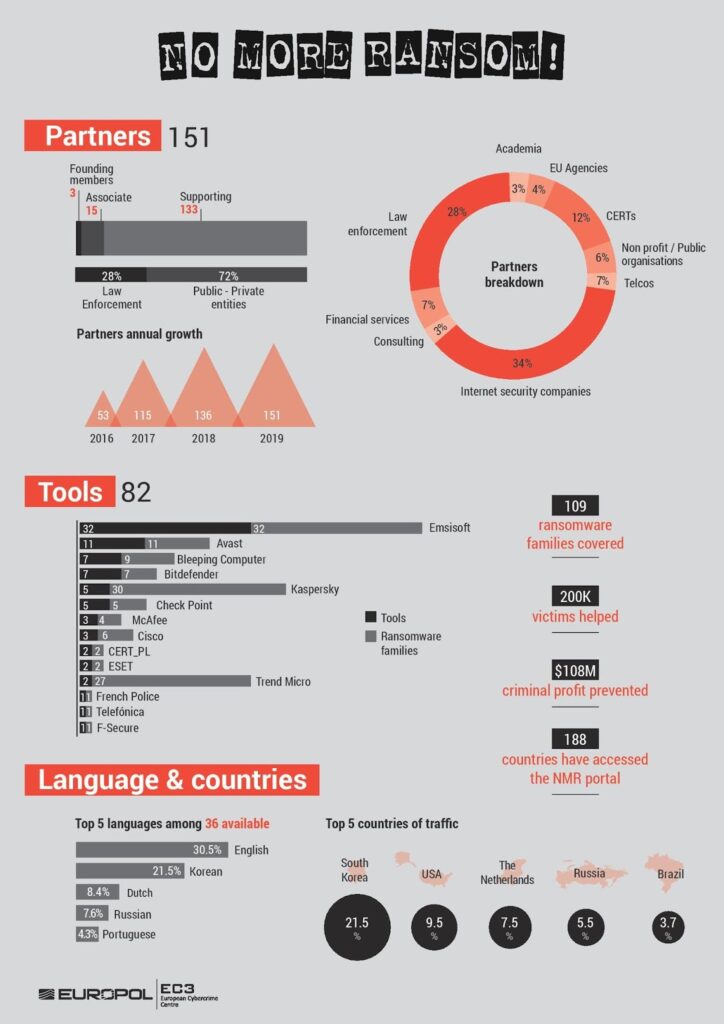
The most common means of Ransomware distribution is through SPAM email which pretend to come from a valid source.
Spam email trigger you to download infected files or click on links.
If you're using webmail services like Gmail, Yahoo or Hotmail/Outlook, then most of these email messages are being filtered and won't reach your inbox.
However, if you're using your own domain and your SPAM filtering is not working well or it's not being set up properly, then most of these emails will reach your inbox.
Rule #6: Did you activate file extension display?
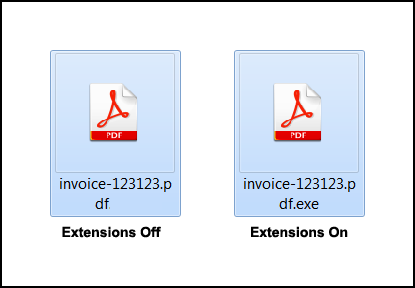
By default, Windows and MacOS do not show the extension of the files when you're browsing a folder. This helps an attacker to trick a user to think an executable file is a common PDF or Word file. The user will click on the file thinking it will open with some text content, however all it does is execute the ransomware shell.
The picture on the left shows an example where a malicious executable file (.exe) pretends to be a .pdf file. By enabling the extension display, we see its real identity (.pdf.exe)Rule #7: Did you open attachments that you do not recognize their sender?
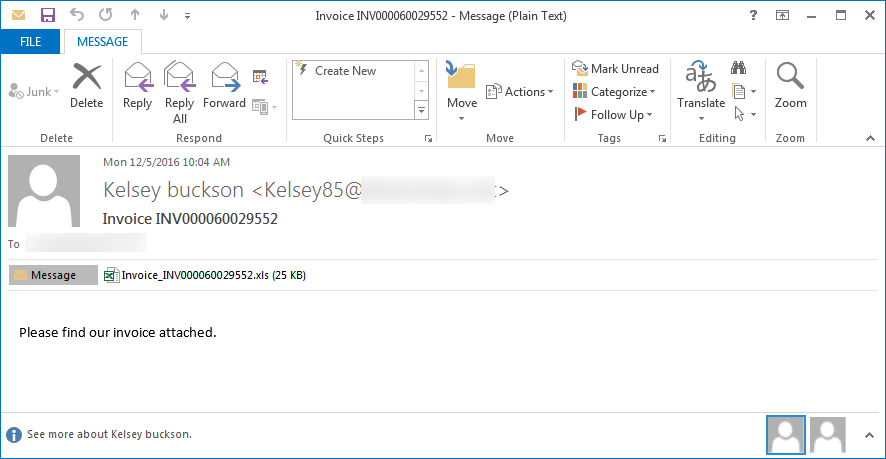
The Ransomware infection is in the attachment.
If you receive an email that contains an attachment and you don't know why someone has sent it to you, do not open it.
In the picture above you can see an email with an attachment that contains Locky Ransomware. As you can see, it has an .xls attachment, it all looks good, and there's is a prompt to open it to check an invoice someone has sent us.
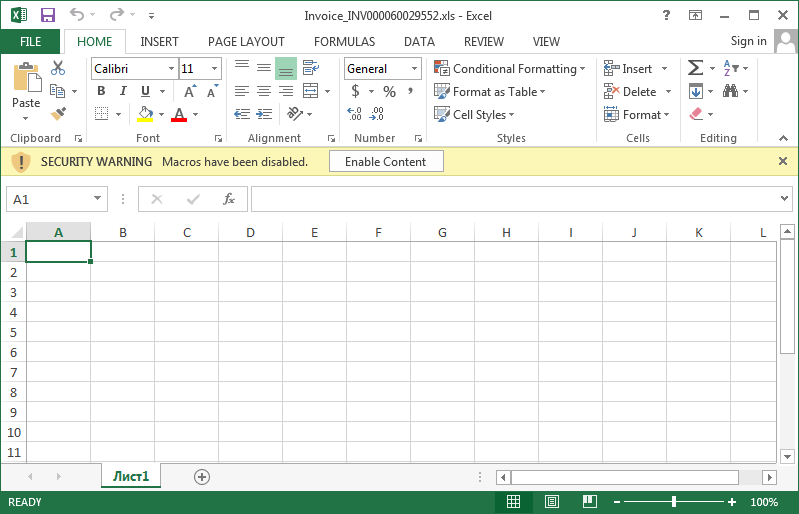
If you make the mistake and open the attachment, you might see another prompt that asks you to enable macros or content ("Enable Macros" or "Enable Content"). Do not do this, it will download Ransomware in your
computer and begin infection and encryption.
Rule #8: Careful with your downloads.
Rule #9: Did you rename vssadmin in Windows?
Rule #10: Did you disable Windows Script Host?

- If you know what these are, it's all good.
- If you don't, we suggest you to disable the ability to execute such files in Windows.
To do this, follow Microsoft's guide from this link: https://technet.microsoft.com/en-us/library/ee198684.aspx |
Rule #11: Did you disable Windows PowerShell?

To do this, go to Start> CMD> Enter and enter the following command to the command prompt και δώστε την ακόλουθη εντολή στο Command Prompt |
If you want to enable it again, just change in the above command the word "Restricted" to "Unrestricted" (without the quotes). |
Rule #12: Are you using strong passwords?
Rule #13: Did you disable Windows Remote Desktop? Did you change the default port?

To do this:
Start>Regedit>enter Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp and find entry PortNumber in the right pane,
Double click it, choose Decimal and change Value Data from 3389 to whatever you want. |
Conclusion: What is Ransomware? 13 Rules and Guides.